
What Is a Hacker?
A hacker is someone who uses their technical knowledge to gain access to systems, networks, or data. The term can refer to individuals with both good and bad intentions. Hackers can exploit vulnerabilities, write code, and manipulate software or hardware in creative ways.
Image suggestion:
Place an image here showing a hacker at a computer with code on the screen—use a neutral tone (not overly dark or “evil”).
Types of Hackers
There are several types of hackers, typically categorized by their intentions:
-
- White Hat Hackers: Ethical hackers who help organizations find and fix security flaws.
-
- Black Hat Hackers: Malicious hackers who break into systems for personal gain or to cause damage.
-
- Gray Hat Hackers: Operate between ethical and unethical lines—often without permission but without harmful intent.
-
- Script Kiddies: Inexperienced individuals who use existing tools to hack without fully understanding them.
-
- Hacktivists: Use hacking as a form of protest or to promote political agendas.
What Do Hackers Do?
Hackers can perform a variety of activities depending on their goals:
-
- Discover and exploit security vulnerabilities
-
- Develop malware or spyware
-
- Penetration testing (ethical hacking)
-
- Data breaches or identity theft
-
- Social engineering (e.g., phishing)
Are All Hackers Bad?
No, not all hackers are bad. While the word “hacker” often has a negative connotation, many hackers use their skills for good. Ethical hackers help secure systems and protect against cyber threats. The cybersecurity industry relies heavily on the skills of white hat hackers.

How to Protect Against Hackers
Protecting against hackers requires a mix of technology and awareness:
- Keep software and systems updated
- Use strong, unique passwords
- Enable multi-factor authentication
- Be cautious of phishing emails
- Use firewalls and antivirus software
- Educate users on cybersecurity best practices
Conclusion
A hacker can be a threat or an asset, depending on their intent and ethics. Understanding the different types of hackers and how they operate helps individuals and organizations defend against cyber threats more effectively.
The Hacking Methodology: Step-by-Step Guide to How Hackers Operate
Understanding the hacking methodology is essential for cybersecurity professionals, IT managers, and anyone concerned about digital security. It outlines the step-by-step process most hackers follow to breach systems. By learning this framework, you can better prepare your defenses and recognize threats early.
1. Reconnaissance (Information Gathering)/Footprinting
This is the first and most critical phase. Hackers collect as much information as possible about the target using public resources or scanning tools.
-
Tools used: WHOIS, Google Dorking, Shodan
-
Types: Passive (social media, websites) and Active (network scanning)
Ø Passive Recon – The only step that is not illegal in the hacker methodology
- Email Addresses
- Phone Numbers
- Social Media Accounts
- Physical Location
Ø Active Recon – Search of vulnerabilities and weakness
- IP Addresses
- DNS Servers
- Open Ports
- Usernames
- Password
- Company Software
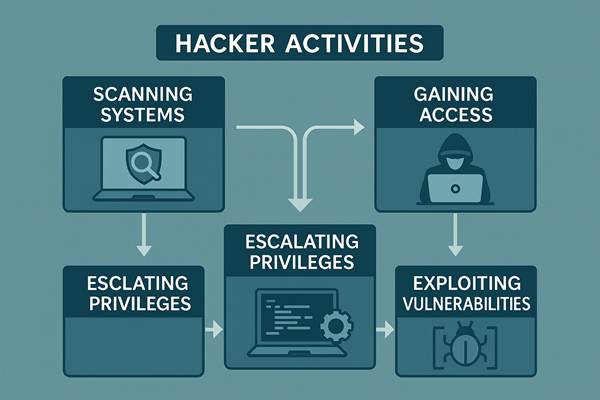
2. Scanning
Next, hackers probe for vulnerabilities. This involves mapping out systems and detecting open ports, services, or weaknesses.
-
Common tools: Nmap, Nessus, Nikto
-
Techniques: Port scanning, vulnerability scanning, banner grabbing
3. Gaining Access/Exploitation
In this stage, hackers exploit the identified vulnerabilities to break into the system.
-
Methods: SQL injection, phishing, malware, brute force attacks
-
Goal: Escalate privileges to gain administrative access
Taking advantage of a vulnerability to gain access
- Phishing Email
- Social Engineering
- Unpatched software
- Weak Passwords
- Malware Injection
4. Maintaining Access
Once inside, the hacker tries to stay undetected and control the system over time.
-
Techniques: Backdoors, rootkits, remote administration tools (RATs)
-
Purpose: To exfiltrate data or use the system as a base for further attacks
5. Clearing Tracks
To avoid detection, hackers cover their traces. This includes deleting logs and masking IP addresses.
-
Tactics: Log file deletion, time-stamp manipulation, anonymizing tools
-
Result: Harder forensic investigation
6. Post-Exploitation / Reporting (for Ethical Hackers)
In ethical hacking, the process ends with documentation and reporting of vulnerabilities found.
-
Deliverables: Risk summary, proof of concept, remediation steps
-
Audience: IT teams, security operations, and executive stakeholders
Final Thoughts
The hacking methodology gives you a roadmap of how attacks are carried out. Knowing these steps helps you create better defenses, train staff, and monitor for signs of intrusion. Whether you’re building a secure system or testing one, understanding this methodology is essential.
